Outlook Enterprise Application
:::note
This article introduces how to use Enterprise Application method to link between Office 365 and WOX. After integration, employees can book rooms on Office 365 (Outlook) or on WOX. The reservation are synchronized.
This is the recommended way to set up Office 365 integrtion. If you're familiar with legacy Exchange integration, or your IT requires, you may use Service Account for integration.
:::
Permissions
Integration setup requires an Microsoft 365 Global Administrator and WOX Location Administrator/Operator roles. These requirements are only used during setup.
If you'd like to know more about why Global Administrator privilege is required during setup, you may consult How and why apps are added to Azure AD - Microsoft identity platform | Microsoft Docs)
The App requires Calendar.ReadWrite permission for all rooms calendar. Additional set up is available for restricting the access only to room resources, so the App doesn't have permissions to access employees' calendars.
Installation
- Login WOX as Space Administrator. Click Settings > Integrations > Office 365
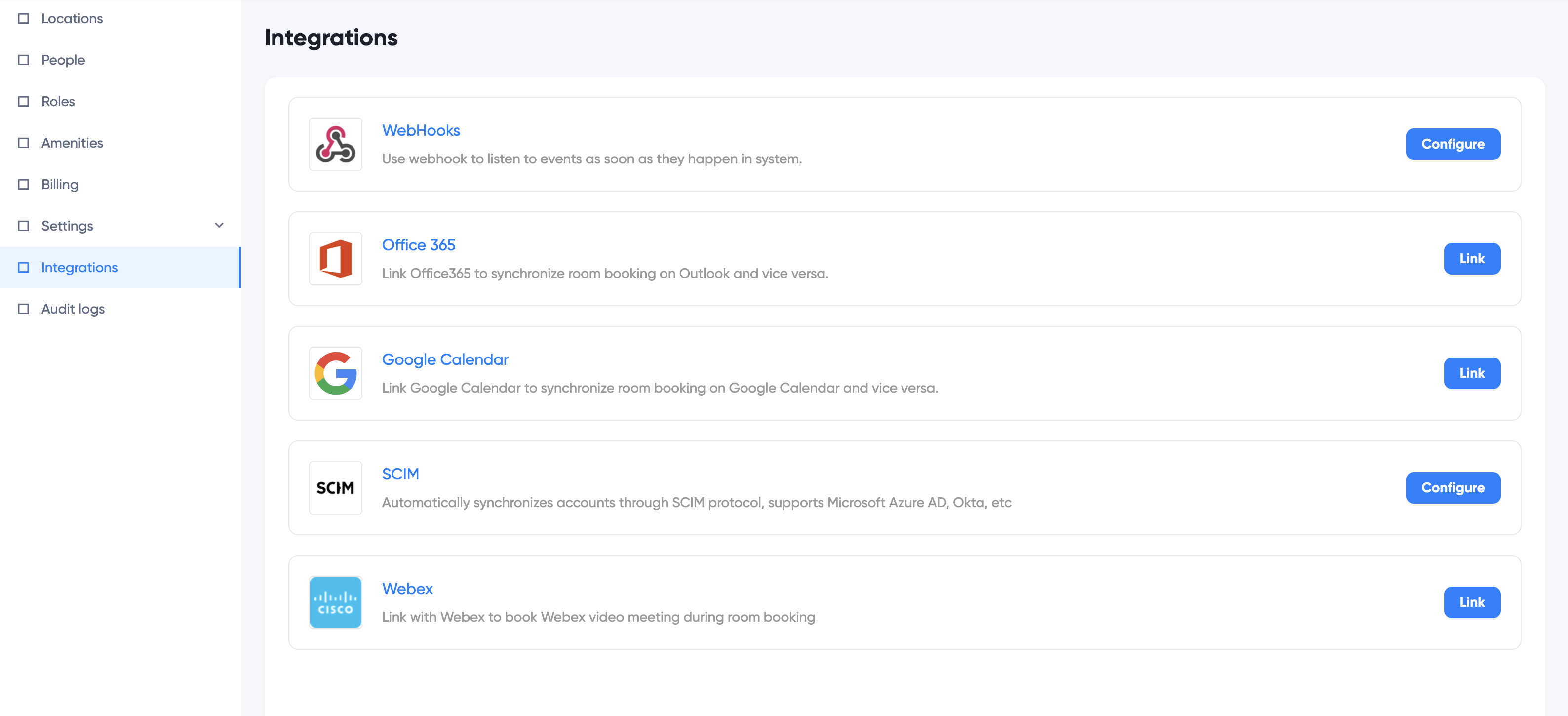
- Click Link, choose which way you'd like to link with Office 365:
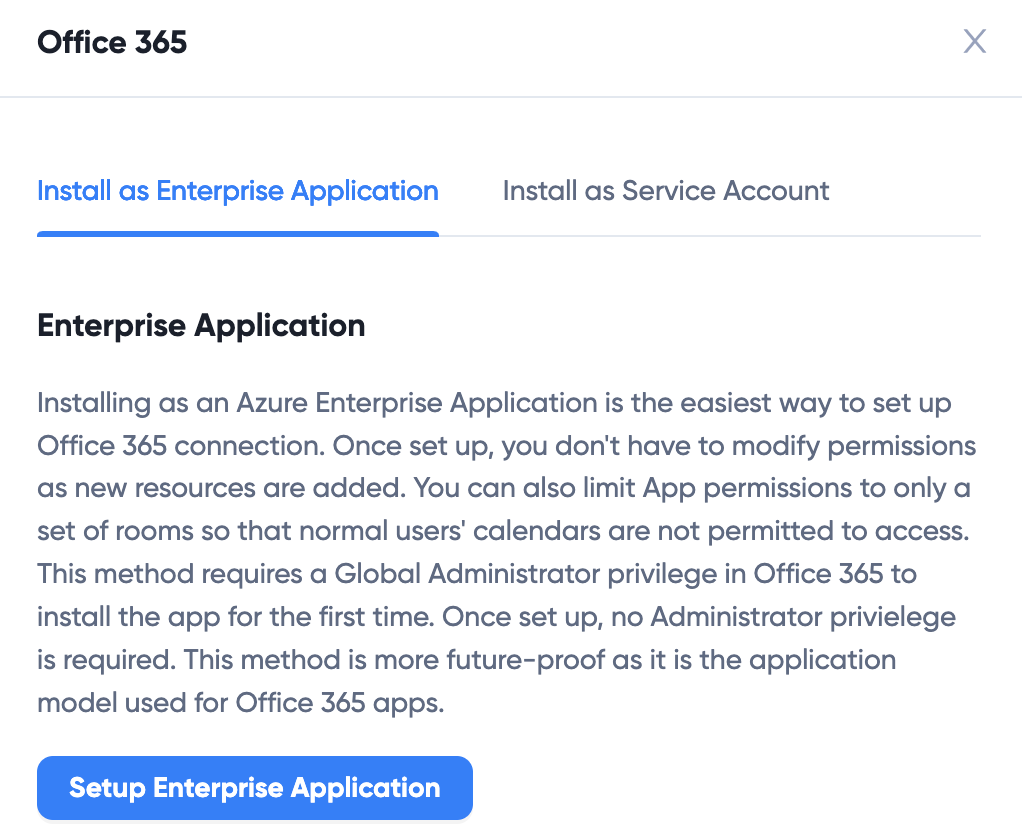
- For Enterprise App, click Setup Enterprise App. If you haven't logined into Microsoft 365, use an Microsoft 365 Global Administrator account to login. After login, a dialog pops up asking for permissions:
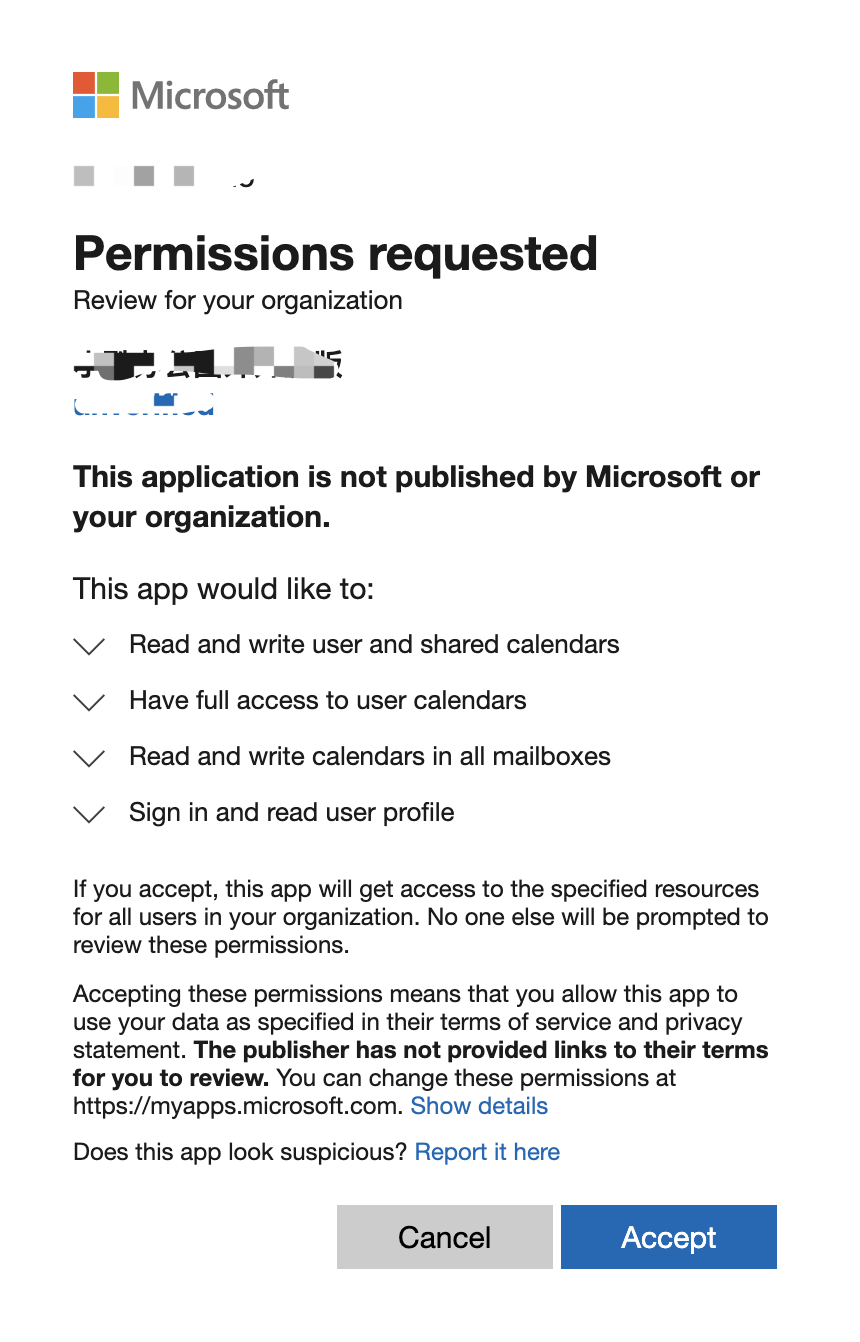
- Click Accept button. After integration, WOX integrations show Office 365 as linked:

Permissions required
Calendars.ReadWriteRestrict App Permissions
After linking Office 365, WOX App has permissions to access all users' calendars (however, WOX only accesses rooms calendars, not employees). If you're concerned, you may follow the steps below to restrict App from accessing employees calendars at all.
Requirements
You need to use PowerShell, with Exchange Online PowerShell addon to perform the steps below.
创建会议室Groups
Login Outlook Exchange admin center. Create an Mail-enabled security Group:
Add all rooms to the group.
Open PowerShell, connect Exchange Online PowerShell, and execute the command below (replace the group email address):
New-ApplicationAccessPolicy -AppId 00941634-fde6-456f-9cfe-e4ca3e23b8e5 -PolicyScopeGroupId <SecurityGroup Email Address> -AccessRight RestrictAccess -Description "Restrict this app to members of meeting rooms group.”Reference: https://docs.microsoft.com/en-us/graph/auth-limit-mailbox-access